





|



|
If SSO Settings option is enabled, users can log into ADSelfService Plus automatically by simply logging into their Windows machine or through a third-party identity provider.
|
|
Single sign-on to ADSelfService Plus is not supported for logins from mobile app or mobile browser. |
ADSelfService Plus supports single sign-on with two types of authentication. They are:
1. NTLM Authentication:
In this method of authentication, users log in to ADSelfService Plus web console using the credentials with which they logged into the machine. To enable NTLM authentication, follow the below steps.
Important: It must be noted that ADSelfService Plus' access URL must be associated with the local intranet sites for automatic logon.
Navigate to Logon Settings (Admin tab → Customize → Logon Settings).
Click Enable SSO checkbox to enable single sign-on in ADSelfService Plus.
Select the NTLM Authentication radio button.
To use NTLM authentication service, a computer account not associated with a physical computer in your network has to be created in Active Directory with a specific password which meets the password policy in Active directory. Click Update Credentials to provide the details of the computer account. It must be noted that the NTLM authentication is domain-based. That is, NTLM authentication can be enabled for a select set of domains of your choice.
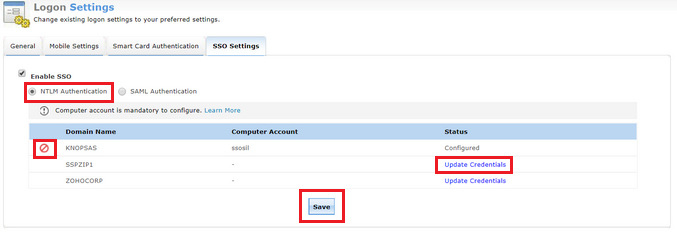
If you already have such a computer account, type the Computer Name and it's Password in the fields provided. You can also create a new computer account by providing the required details and selecting the Create this computer account in the domain checkbox. Enable or disable the computer accounts by clicking on the enable/disable button.
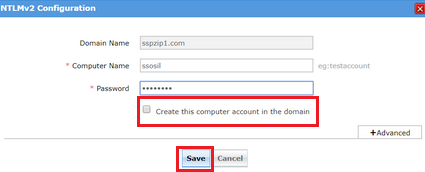
Click Save.
In case you've installed ADSelfService Plus in a machine that does not belong to the domain you have chosen, click the Advanced button and specify the DNS Server and DNS Site of the domain.
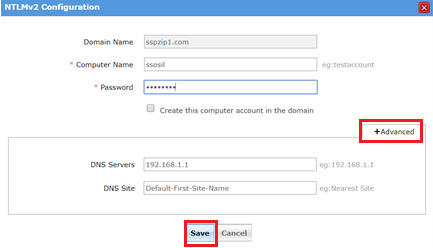
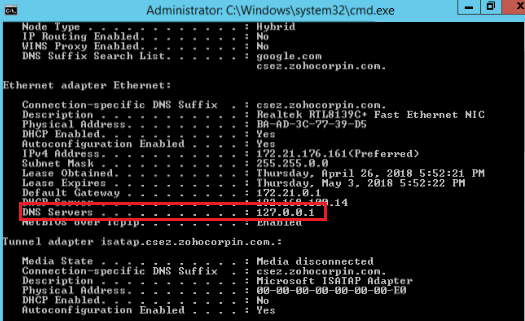
A. How to find the IP address of the DNS Servers?
In a machine which belongs to the domain you've selected, open the command prompt and type ipconfig /all and press enter.
Enter the IP address displayed under the DNS Servers in the respective field.
B. How to find the DNS Site?
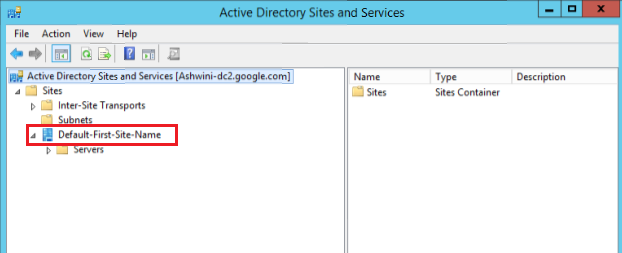
Navigate to Active Directory Sites and Services.
Enter the DNS Site containing the domain controller of the selected domain in the respective field.
C. How to add sites to the Local intranet zone?
The required configuration can be applied in two ways.
Method 1: Using a group policy (supported on Google Chrome and Internet Explorer)
Create a new Group Policy Object and navigate to User Configuration → Administrative Templates → Windows Components → Internet Explorer → Internet Control Panel → Security Page → Sites to Zones Assignment list. Select Enable.
Click Show to display the zone assignments. Enter the access URL in Value name and relate it to the trusted sites by entering the number 1 in Value, and then click OK.
Navigate to User Configurations → Administrative Templates &rarr All Settings → Logon options. Select Enable.
From the Logon options list, click Automatic logon only in Intranet zone, and then click OK.
Method 2: Manual configuration
Google Chrome:
Navigate to Settings → Advanced drop-down → System module → Open proxy settings.
Click the Security tab and select the Local intranet icon.
Click the Sites button and proceed to enter the access URL of ADSelfService Plus in the required field, and click Add.
Internet Explorer:
Navigate to Tools → Internet Options → Security.
Click the Security tab and select the Local intranet icon.
Click the Sites button and proceed to enter the access URL of ADSelfService Plus in the required field, and then click Add.
Mozilla Firefox:
Type about:config in the address bar and hit the enter key to display the list of preferences. If there's a warning message displayed, click the I accept the risk button to proceed.
Navigate to the network.automatic-ntlm-auth.trusted-uris preference.
Double-click the preference and enter the access URL of ADSelfService Plus. For example: selfservice-5994:8888
Click OK.
2. SAML Authentication:
ADSelfService Plus supports one click access to its web console through SAML-based identity providers (IdPs).
After enabling SAML-based SSO option, every time a user attempts to access ADSelfService Plus' web console, the IdP receives the authentication request. IdP authenticates the user, and after successful authentication, the user will be automatically logged into the ADSelfService Plus portal. If the user is already logged in to the identity provider, when a user tries to access ADSelfService Plus, they will be granted access automatically.
Prerequisites:
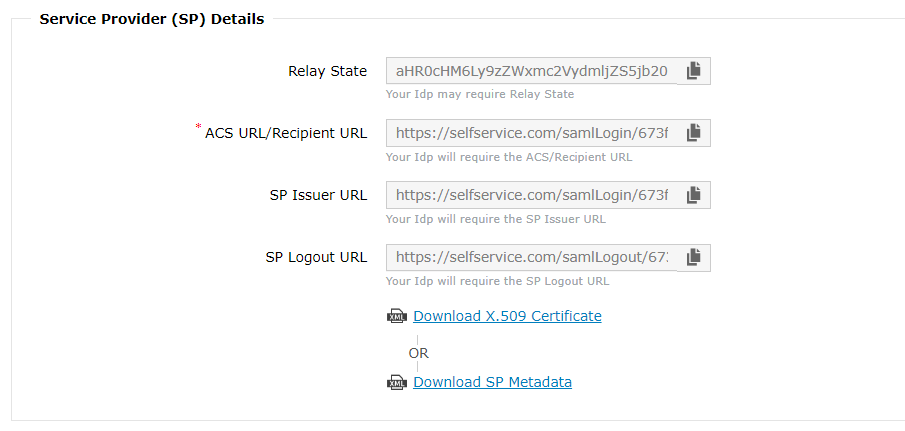
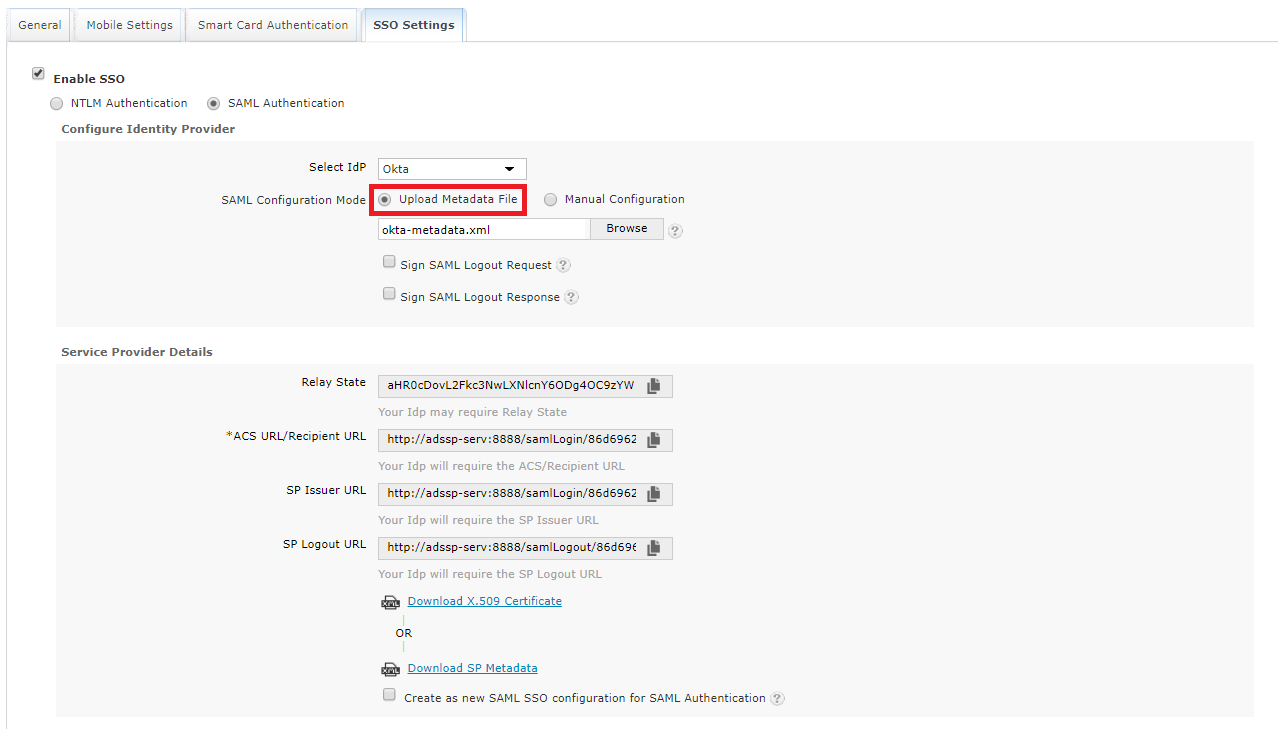
Log in to ADSelfService Plus web console as an administrator. Navigate to Admin tab → Customize → Logon settings → SSO Settings tab. Click the Enable SSO checkbox and the SAML Authentication radio button. Either download the X.509 Certificate file, or get the required data by copying the Relay State, ACS URL/ Recepient URL, SP Issuer URL, and SP Logout URL. You'll need this information while configuring your identity provider.
The SAML-based identity provider that you intend to use must have ADSelfService Plus as one of its SAML supported applications. If it is not supported by default, you can add ADSelfService Plus as a new application in your identity provider. Find the steps to add a new application in Okta, OneLogin, and ADFS by clicking on the respective links. For other identity providers, contact their support team for further assistance.
Log in to your identity provider with admin credentials and navigate to ADSelfService Plus from the list of applications provided. Either download the Metadata in XML format, or get the required data by copying the Issuer URL/Entity ID, IdP Login URL, IdP Logout URL, and the X.509-certificate. You'll need this information while configuring ADSelfService Plus for logon SSO.
Step 1: Service Provider Configuration (ADSelfService Plus)
Log in to ADSelfService Plus web console with admin credentials.
Navigate to Admin tab → Customize → Logon settings → SSO Settings tab.
Check the Enable SSO checkbox to enable single sign-on in ADSelfService Plus.
Click the SAML Authentication radio button to enable SAML configuration in your domain.
Select the identity provider of your choice in the Select IdP drop-down box. If you have selected Custom SAML from the drop-down list, you must type in the IdP name and upload IdP logo in the respective fields.
There are two SAML Configuration Modes: Upload Metadata File and Manual Configuration.
Select Upload Metadata File if you have downloaded the IdP metadata file from the identity provider. (Refer step 3 of Prerequisites)
Click Browse to upload the IdP metadata file.
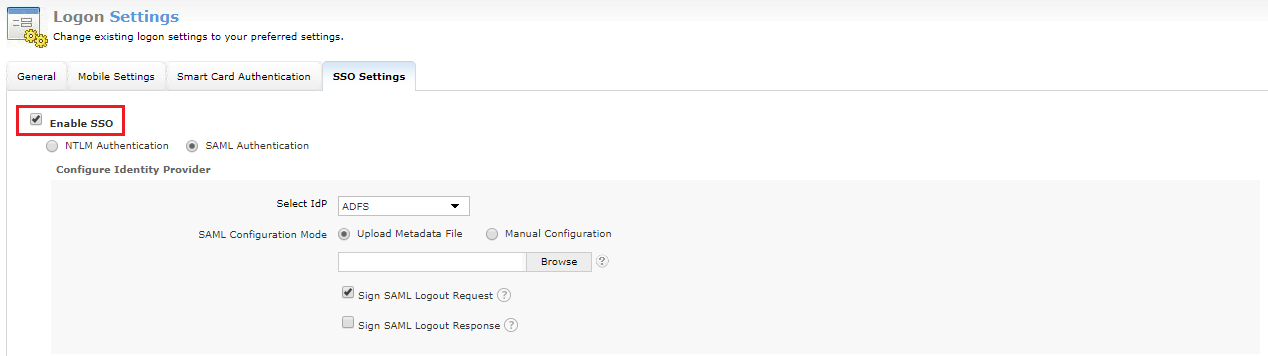
Select Manual Configuration to manually configure the URLs and certificates.
Select the Sign SAML logout Request option to sign the logout request which goes from ADSelfService Plus to the SAML-based identity provider. Know more.
Select the Sign SAML Logout Response option to sign the logout response that goes from ADSelfService Plus to the SAML-based identity provider. Know more.
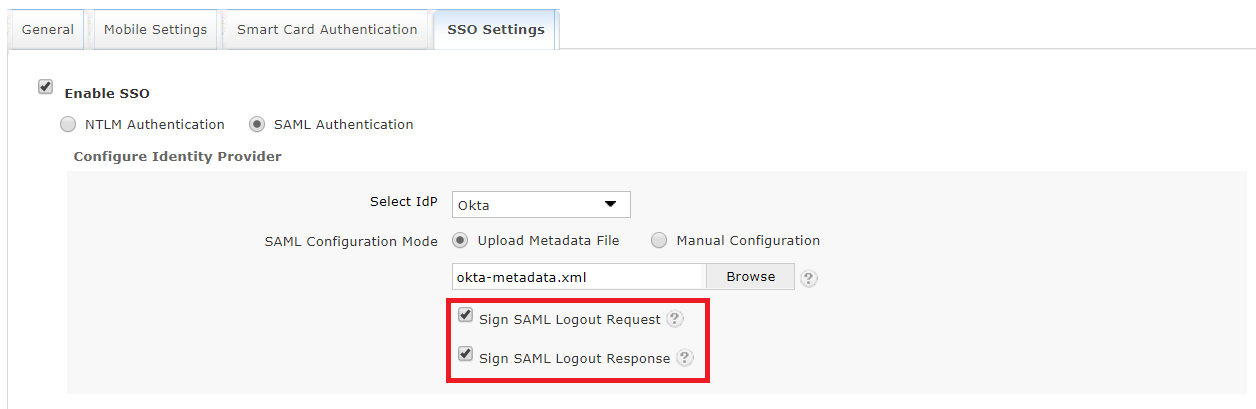
Click Save.
|
|
By default, ADSelfService Plus maintains the same SAML authentication configuration for logon SSO and multi-factor authentication.Select the checkbox to create a new SAML SSO |
|
|
|



|



|